AI in ASOC
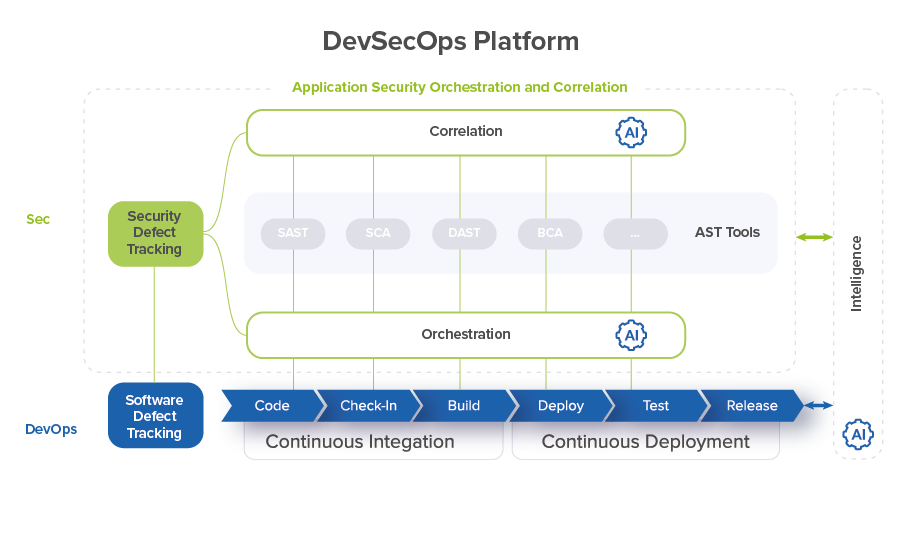
DevSecOps makes software security a core part of the overall software delivery process. The DevSecOps platform integrates application security testing (AST) tools into existing CI/CD pipelines for application development, enabling the transition from DevOps to DevSecOps.
According to Gartner, solutions to enhance security testing and provide protection and insight into the use of software systems are gaining increased interest. Nowadays, Application Security Orchestration and Correlation (ASOC) tools have reached the Peak of Inflated Expectations (see detailssee details). ASOC practice integrates the AST practices and tools across Software Development Life Cycle (SDLC) and performs correlation analysis of the security issues found by AST tools.
In addition to the orchestration and correlation itself, Gartner sees an additional benefit in using ASOC tools to provide risk reports on the security and business risks caused by applications (see detailssee details).
However, ASOC tools have an ability to offer more benefits. ASOC tools integrate security tools with software engineering tools and enable consolidation of all data gathered within the continuous secure software engineering process. During the orchestration and correlation processes, the DevSecOps platform collects a wide range of data related to the development, testing and security of the developed application in real time. The availability of this data makes it possible to provide immediate feedback to the DevSecOps platform and enable intelligent control of the entire Secure Software Engineering Lifecycle also in real time.
Thus, a timely decision is to add new capabilities to the ASOC for analyzing all collected data. To implement this, in the ASOC tool, you need to create another functional module for aggregating, storing and analyzing the collected data. To implement such functionality, the following steps are required:
1. Collect the raw data from security tools and software engineering tools and store it in a data warehouse (DWH).
2. Define a set of metrics based on the collected data.
3. Define a set of Key Performance Indicators (KPIs) by adding business context to the metrics.
4. Implement dashboards to manage the DevSecOps platform based on the raw data, metrics and KPIs.

However, just data analytics is no longer enough today. There is an opportunity and even a necessity to switch to Artificial Intelligence (AI) technologies.
Driven by AI, leveraging data to make informed decisions helps organizations be adaptable to future changes while implementing DevSecOps, understand user behaviors, and enhance application delivery. Continuous improvement is key to getting better at DevSecOps implementation and AI-driven tools and automation become the enablers in the process.
To do this, the steps to implement the functionality of the add-on module for working with data should be modified as follows:
1. Collect the raw data from security tools and software engineering tools and store it in the data warehouse.
2. Define a set of metrics based on the collected data.
3. Define a set of KPIs based by adding business context to the metrics.
4. Process the raw data, metrics and KPIs using technologies based on Artificial Intelligence (AI) and Machine Learning (ML).
5. Implement dashboards to manage the DevSecOps platform based on the processed data and metrics.

Working with DevSecOps data and managing it using AI/ML technologies enables transition of ASOC to AI/ML driven DevSecOps platforms.
With AI/ML technologies, a vast volume of raw data collected by the DevSecOps platform in DWH can be thoroughly analyzed. These technologies enable in-depth data analysis as well as trends discovery and forecasting. AI/ML allows to organize analysis of collected data in real time and provide a feedback loop to timely correct the DevSecOps processes.
In terms of the ASOC practice, AI/ML helps to improve the work of both orchestration and correlation capabilities.
Correlation
Make Application Security Testing a True Part of Software Engineering Pipeline
AI/ML enables implementation of the Application Vulnerabilities Correlation (AVC) functionality based on the data driven security issues correlation engine. The correlation engine incorporates the ML model that is trained to automatically filter false positive results, identifies duplicates and similar issues, and groups them to the single defect based on information about security issue details, source code and application context.
This significantly reduces Mean-Time-To-Resolve for security issues that are identified, keeps security experts and software engineers focused on really critical vulnerabilities, and helps developers improve the speed with which they identify threats to their software.
Automated Remediation Guidance
Manual remediation of security issues delays releases, takes valuable resources, and as a result, quite negatively impacts overall Time-to-Market. While many coding vulnerabilities are identified, there are always issues – even critical ones – which still have relatively simple fixes. AVC engine identifies and prioritizes security defects in the most efficient way, and as a step further, AI/ML technology can help developers understand what they’re doing wrong and what they need to do to fix these particular vulnerabilities by providing automated remediation guidance; for example, by supplying correct piece of code / clean version of open-source component as a suggestion.
One capability of ASOC is application security issues data collection from various sources (scanners) through different techniques (SAST, SCA, DAST, IAST, etc.) which allows you to recreate a mutually exhaustive picture on real software vulnerabilities introduced by developers. Having AVC implemented from one side and enriched by detailed and granular security coding standards and guidelines for particular programming language from another, AI/ML technology can offer software engineers customized secure code patterns based on the organization’s unique DevSecOps landscape. This assists in automated vulnerability remediation and prevention of security issues introduction in source code further.
Continuous monitoring is a core feature of DevSecOps, and AI/ML adds more advanced technological backup to power this feature.
Orchestration
Automate Quality Gates
Quality gates enable the decision making on whether a build can be moved into the next stages of the software development lifecycle and deployed to the development, test, pre-production or production environments. To achieve faster and continuous releases, automating the quality gates at each stage of the pipeline helps automate the Go/No Go decision of a build into various environments. Automated quality gates can include various numbers of security practices and their configurations can be dynamically adjusted depending on the pipeline stage. Software quality can be managed by setting the quality gates in the CI/CD security pipelines and tuning the quality gate criteria based on the analysis of collected data and quality metrics.
Pipeline as Code
For large DevSecOps implementations, managing the end-to-end CI/CD pipeline as code provides clear advantages. Pipeline as code enables various delivery teams to trigger, manage and track their deployments better. Mature ASOC solutions provide the capability to build security pipelines out of the box by one mouse click. Adding AI/ML technology allows automated discovery of software engineering assets with corresponding artifacts and generation of security pipelines for them with intelligently defined quality criteria.
Deliver at Speed
Once all the pieces of the CI/CD puzzle are put together, being able to track the speed of delivery, from commit to release, is important. To be able to release every day, or multiple times a day, requires the various stages of the pipeline to be optimized for faster feedback and completion. If your pipeline cannot fail fast, you cannot achieve continuous delivery speed.
Ultimately, AI/ML enables proactive management of the whole DevSecOps platform at all stages of the SDLC:
Security Requirements and Compliance Management
For many large enterprises, application security compliance requirements are very important. It is necessary that a holistic approach is taken during automation, to include compliance requirements as part of automation. The automated compliance checks should ensure all criteria are met and application/features can be released into production.
AI/ML technologies help to establish a continuous monitoring process with predictive analysis capabilities based on the status of quality gates applied for particular software artifacts (source code, library, Docker image, build, release, etc.) on a particular CI/CD stage.
Next Generation DevSecOps Platform
With this said, ASOC solutions supporting fully automated AI/ML-driven secure software engineering practices represent themselves the next generation of DevSecOps platforms that can solve today's application security challenges for software of any architecture and complexity.
Maverix is the only next generation DevSecOps platform that implements the ASOC practice and adds DWH, metrics, KPIs and elements of AI/ML to the DevSecOps processes on top.