ASOC Problem / Solution
Problem / Solution
When adding security testing using AST tools, two problems arise: how to handle the flow of security issues, and how to integrate AST tools into the existing DevOps process and shift to a DevSecOps process?
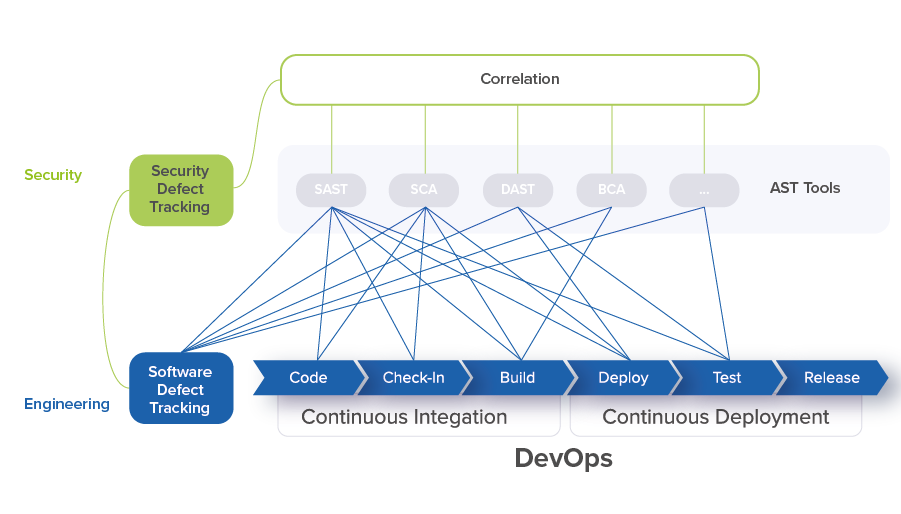
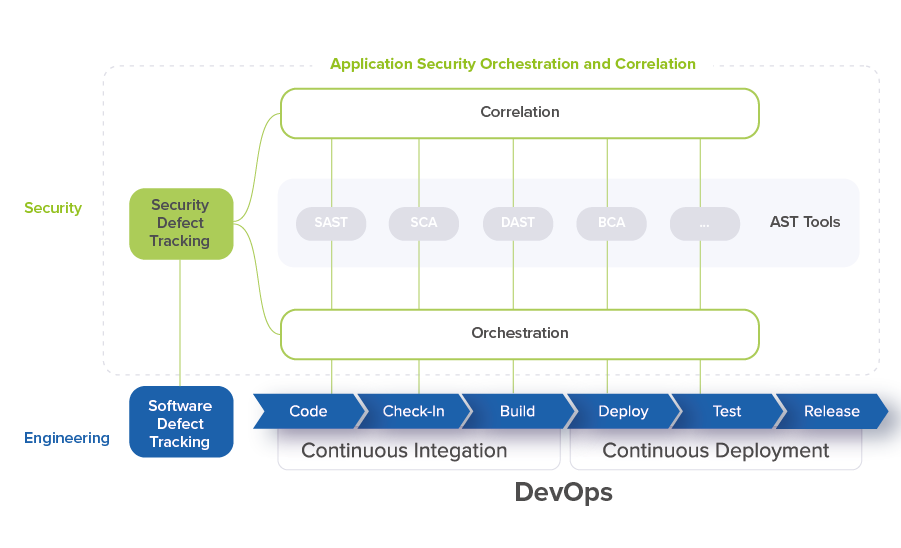
The Application Security Orchestration and Correlation (ASOC) tool addresses these two problems. ASOC integrates AST tools into the Software Development Life Cycle (SDLC) and performs correlation analysis of security issues discovered by AST tools.
Correlation
Software engineers utilize DevOps processes and tools to develop code, fix software defects, check-in code, build, deploy, test, and release into production.
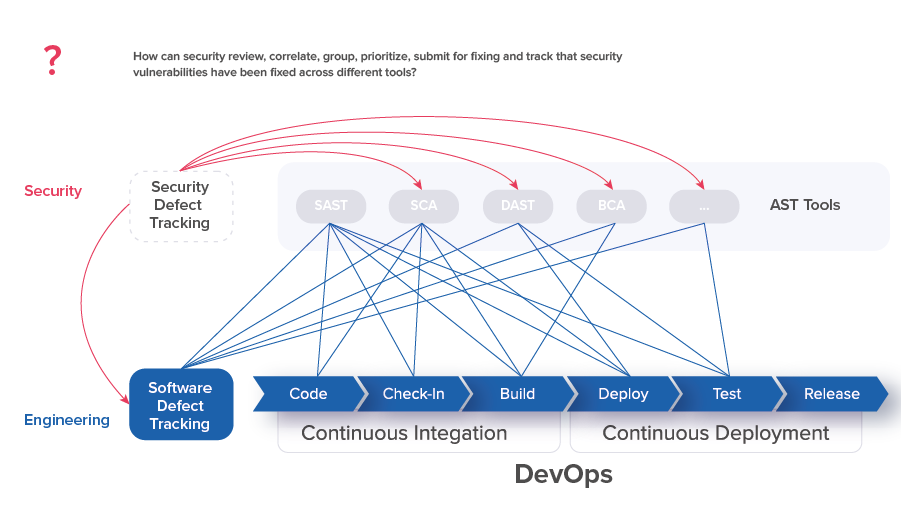
Security Engineers follow complementary processes, including identifying security issues and validating bug fixes. At the right DevOps stage, teams use AST tools to identify security issues for security team review, filter out false-positives, group issues into defects, prioritize defects for resolution, and submit security defects to defect tracking.
After security defects are fixed and the related code is checked-in, security scanning is reinitiated, new security vulnerabilities are identified and previously submitted security defects are checked and resolved.
To manage security processes, security team pulls together not only the security defects information related to the vulnerable source code – e. g. name of the file, version of it in the version control system and line numbers – but also take into account broader contexts, such as stage of CI/CD pipeline, the operating system’s component dependencies, open source libraries, application packages, Docker containers involved, and then check if the artifacts from the repository were modified. Without these processes it is difficult to reproduce an original defect and make a conclusion whether it was fixed. These verifications should be embedded into existing CI/CD pipelines in order to avoid compromising automation of the build and deployment process.
With multiple security tools, information should be pulled together into a single pane of glass tool where all security defects can be easily reviewed and tracked for resolution.
To enable comprehensive data collection and analysis, security teams need to create integration scripts to enable automation and data visibility. With the ASOC tool the teams no longer need to write significant amount of proprietary scripts to implement DevSecOps.
Orchestration
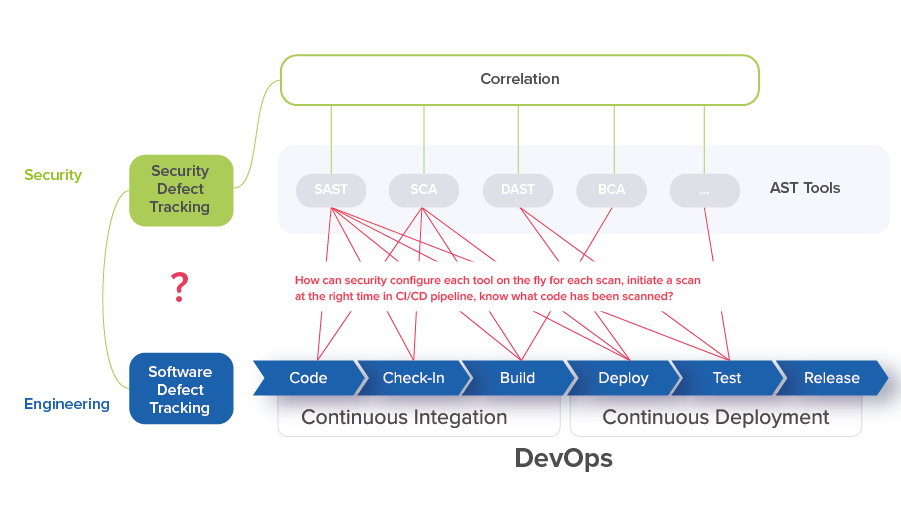
Security and development teams need to know the stage of DevOps in the CI/CD pipeline and what code has been checked-in for the current build. The security engineers then determine whether the fixed security defect is in the checked-in code already and that this build can be used to validate that the security defect is not there anymore. Developers should have the same information in order to resolve security defects and verify fixes using unit tests methodology, or, even better, trigger the execution of security checks in the CI/CD pipeline to see the result of the applied fix.
That’s why organized in an agile fashion, two-way communication between security and development teams is important to proper security hygiene and the ultimate implementation of DevSecOps.
To have DevSecOps processes under control, the security team needs to collect multiple metrics including mean time to detect, mean time to resolve and mean time of vulnerability in production. The team needs to tune the processes so time to detect and time to resolve are shorter than a typical two-week sprint, in a matter of days. This can only be achieved when all scans are triggered automatically and data is collected and consolidated centrally.
A correlation tool will not know what stage of DevOps CI/CD pipeline is in and what code has been checked-in for a current build. Thus, the process of figuring out when to run a scan to reconfirm that a security defect has been fixed cannot be determined programmatically, and security testing becomes dependent on manual processes. Managing the whole cycle would, in that scenario, take too much time. There also are technical challenges with integrating security tools into an engineering environment and with defect tracking tools. For most teams it is very difficult to dedicate the required effort to track all these steps manually at the speed of DevOps.
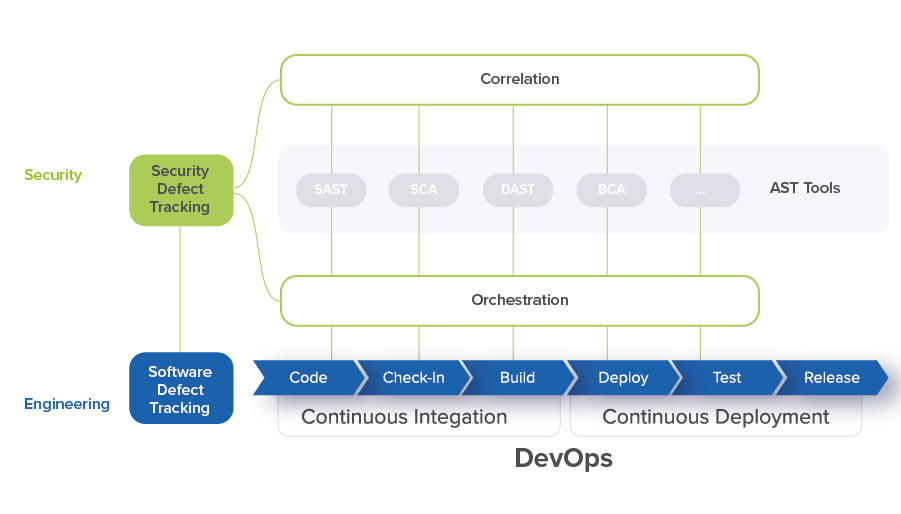
Orchestration is required to connect security processes with DevOps CI/CD pipelines in order to initiate a security scan by specific security tool on specific branch of code with specific security tools configurations.
Security needs to have access to code repository data to support key security metrics in reports and dashboards. Correlation tools only deal with security issues and defects and don’t collect lines of code information. Only by having this information can a security team automatically calculate security defects density per 1,000 lines of code – an important security indicator.
Being able to track when a security vulnerability gets discovered, when it is submitted to developers for fixing, when the fixed code is checked-in, and when it reaches the stage of a build that is deployed is critical to the effective use of AST tools. They need to rescan to validate that security defects are fixed. By knowing this timeline, it’s also possible to understand if this vulnerability escaped into production when it was fixed, or if it was fixed in pre-released code and the vulnerability was fixed in the same sprint as when it was detected.
An integrated Application Security Orchestration and Correlation (ASOC) tool addresses all of these problems.
ASOC tools provide all of the required integrations on a single platform for both triggering security scans and consolidating security issues. They offer a single user interface to review, track and group security issues, and submit security defects into a software defect tracking tool. They have bi-directional synchronization to track the status of each defect.
These tools track all configuration information from AST tools and can configure scans. They have simple snippet-based integration into DevOps CI/CD pipelines and create their own security pipelines automatically. What’s more, they have integration with engineering tools to collect engineering data to enable better analysis of security defects.
To keep the DevSecOps process under control, ASOC tools perform additional development and security data collection from all AST and software engineering tools integrated into the DevSecOps system. This additional functionality helps to implement DevSecOps analytics and, in the case of AI, enables the integration of actionable intelligence in key processes. A detailed description of this approach can be found in the “AI in ASOC” article.