How the ASOC Tool Works
DevSecOps Platform
One of the main challenges for software development is reducing time to market. Rapidly changing business conditions have led to an evolution of software development processes from the Waterfall model into Agile and from Agile into DevOps.
Another big challenge is ensuring information security. Currently, information security practices are often not properly integrated into DevOps. This situation creates a bottleneck in software development and, therefore, in business too.
A transition from DevOps to DevSecOps requires embedding security tools and practices into the software development cycle. DevSecOps is a software engineering process with enabled security controls:

Maverix is an automation platform which provides a plug and play transition from DevOps to DevSecOps. It is focused on application security and manages the application security testing end-to-end. The platform provides out of the box integrations with software engineering and application security testing (AST) tools. Maverix integrates security checks performed by the AST tools into application development CI/CD pipelines. It performs the role of an application security automation hub that enables smoothly shifting application development projects from DevOps to DevSecOps based on the existing project toolchain and DevOps practices.

ASOC Tool
Today, application security is a mature discipline that covers more than a dozen practices. Most of these practices are related to application security testing and application protection. A detailed description of each practice is provided in the “Technology—Application Security Practices” article.
In terms of application security practices, Maverix implements the Application Security Orchestration and Correlation (ASOC) practice, which ensures end-to-end integration of the AST tools with software engineering tools and provides correlation analysis of the security issues found by AST tools.
Orchestration and correlation are the key Maverix product features, as well as the intelligence in DevSecOps data analytics.
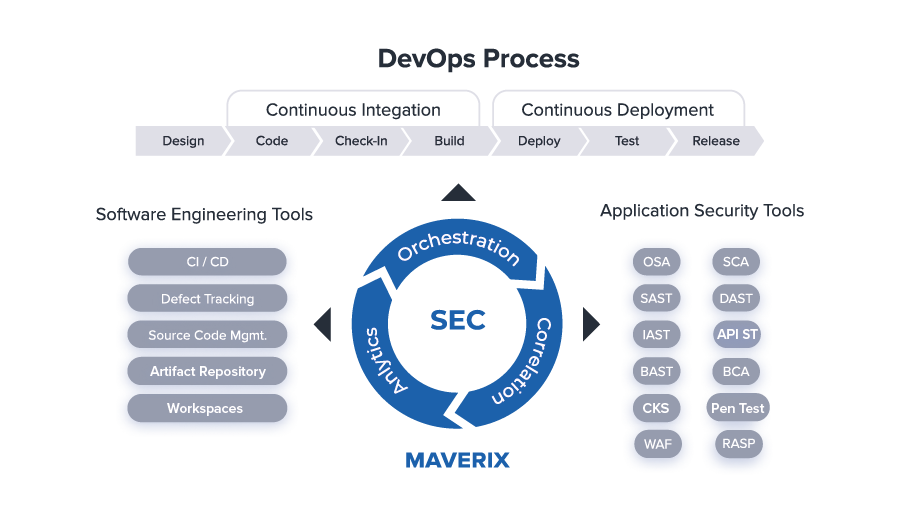
Let’s consider how the ASOC tool works using Maverix as an example.
Orchestration
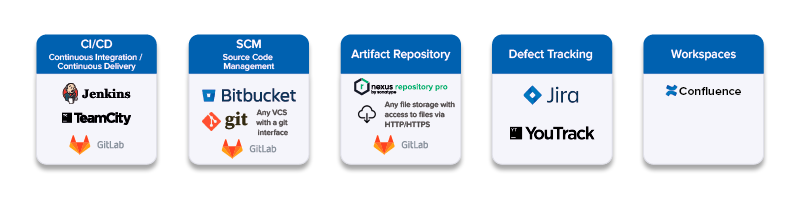
Orchestration allows you to create and manage security pipelines. Maverix provides out of the box integrations with a number of engineering tools and AST tools intended for different DevSecOps areas of application development. As of today, the following software engineering tools grouped by types can be integrated by Maverix:
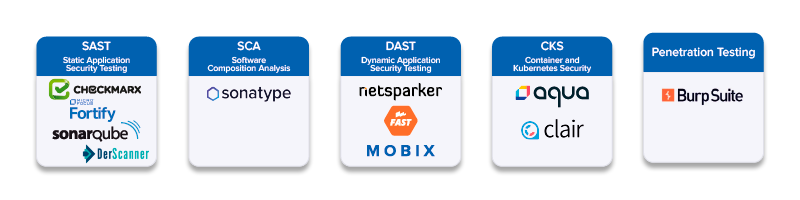
The following AST tools grouped by practices can be integrated by Maverix:
Integration with the tools includes:
- Bi-directional communication via REST API
- Bi-directional synchronization
- Automated configuration, settings management, and setting task for AST tools
Maverix creates, configures and executes security pipelines including configuration of AST tools for each individual security scan. It initiates the scans at the right point of time and aggregates found security issues for further analysis and prioritization. Maverix provides integration of newly created security pipelines into the existing DevOps process. For example, security pipeline with the SAST, SCA and DAST security scans added by Maverix to the existing CI/CD pipeline can look like this:
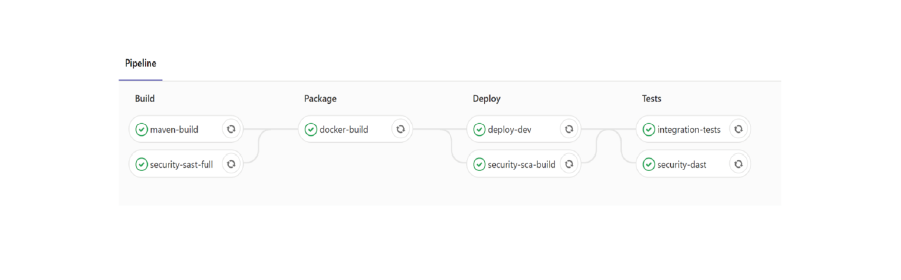
The process of security scans integration into existing CI/CD pipelines using Maverix is well defined and easy to implement. To connect to CI/CD tools such as Jenkins or TeamCity, and to embed a security check in an existing CI/CD pipeline, Maverix provides a code snippet (approx. 10 lines of code) that can be copy-pasted into the existing CI/CD pipeline. This code snippet calls the scripts that pick up all the required security pipeline configurations from the Maverix database. With a code snippet embedded, the CI/CD tool can automatically run the security pipeline configured in Maverix. The CI/CD tool launches all software engineering and AST tools as defined in the security pipeline and sends the results to Maverix. An example of a code snippet added by Maverix is highlighted in blue in the following figure:
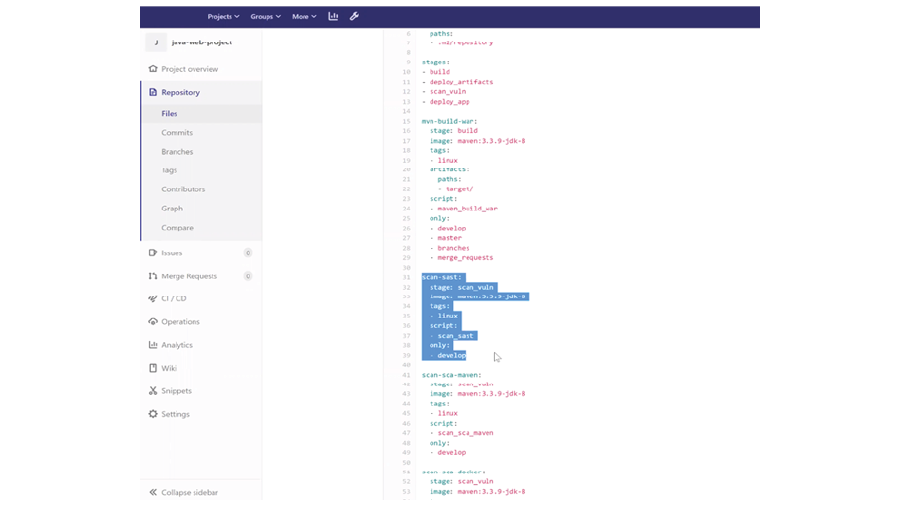
Correlation
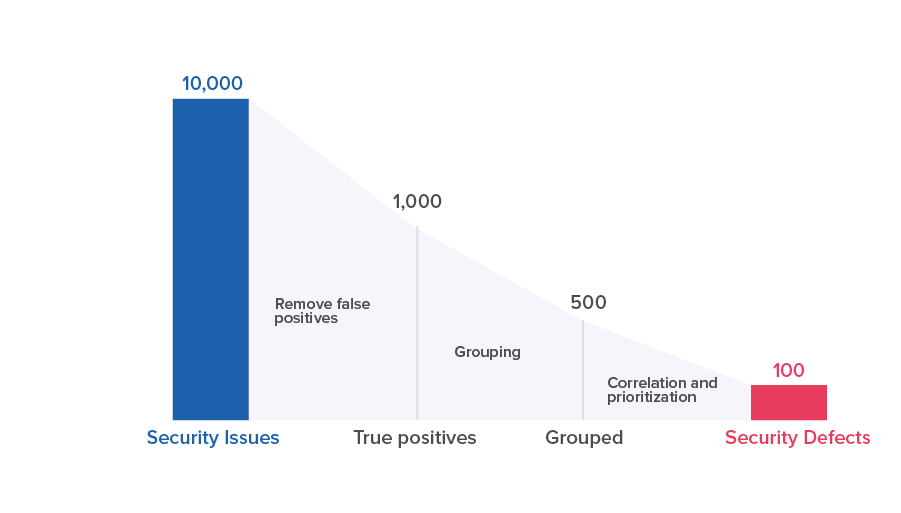
Correlation allows you to work with security issues and convert them into security defects for the development team. Maverix collects security issues generated by different AST tools, standardizes the issue description, enhances them with engineering information, and consolidates everything in a common workspace. It enables a security engineer to triage security issues, group them into security defects, and synchronize with a defect tracking system.
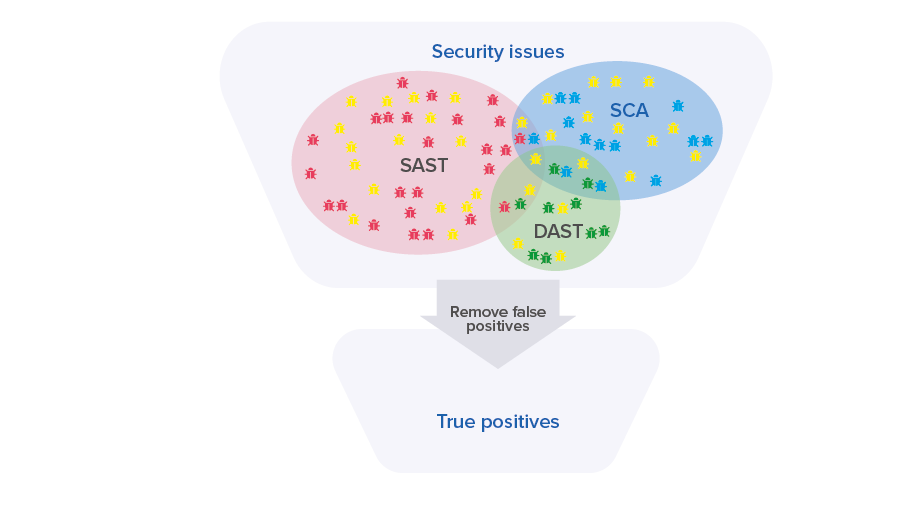
Working with many false positives generated by the AST tools is a big issue in application security testing. To address this problem, Maverix implements a machine learning-based three-stage security issues processing algorithm.
In the first step, Maverix automatically reviews issues that were generated by the AST tools and filters out false positive issues. This allows to remove the false positives from consideration and select only true positive issues (in the figure below, false positive issues found by all AST practices are marked in yellow, and true positive issues are marked in the color that corresponds to the AST practice color—orange, blue, and green):
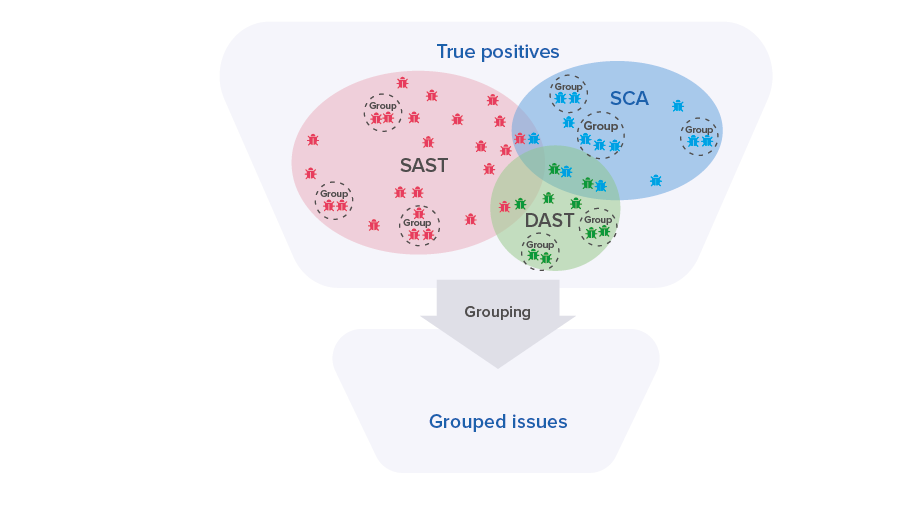
At the next stage, Maverix groups similar issues which can be fixed all together at the same time to handle them as one issue. Grouping is applied both for security issues found by one AST tool, and for security issues found by several AST tools:
Different AST tools could find and generate the same true positive issues. Maverix determines correlation between the issues found by all AST tools. Implementation of an Application Vulnerability Correlation (AVC) mechanism enables Maverix to apply correlation rules and detect issues found by several AST tools:
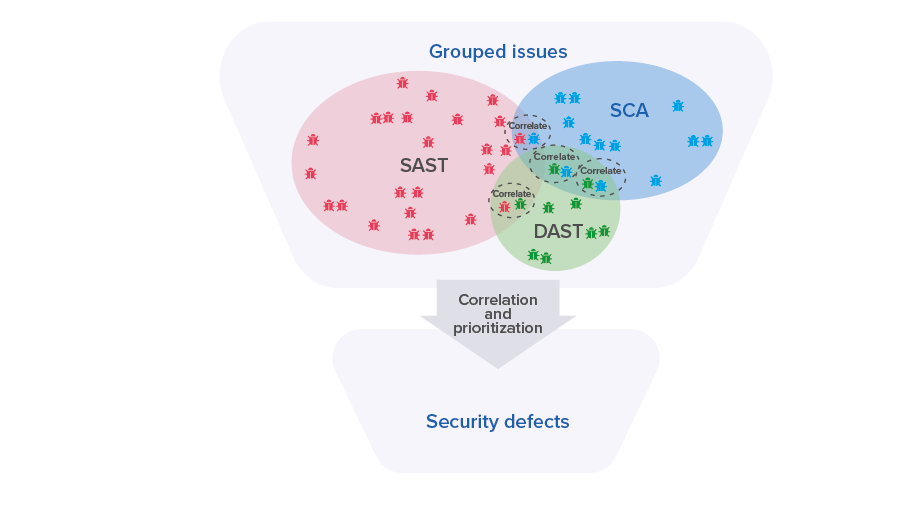
Each issue that was found in multiple ways by different AST tools is more likely to be a security defect. This allows to prioritize these issues and to reduce the effort for analysis by security engineers. Maverix also prioritizes all issues by severity, from high to low. It helps security engineers to filter for prioritized issues. Thus, security issues can be quickly triaged. The most important security issues can be selected and converted into security defects. Prioritizing issues significantly simplifies work on the security issues backlog:
Intelligence
DevSecOps data analytics allows you to analyze applications’ security status across the entire organization’s teams and applications. Maverix aggregates engineering and security data in a data warehouse (DWH) and offers a set of metrics, dashboards and reports to work with this data. It implements unique AI-based DevSecOps data intelligence engine for data collection, aggregation and analysis. Maverix uses both software engineering tools and AST tools as a data source. It implements data visualization through a set of metrics and dashboards.
Thus, management, development, operations and security teams have complete insight in security and software engineering. This allows to implement end-to-end DevSecOps process analytics and data driven control of the DevSecOps platform.