Product Overview
Maverix is a DevSecOps platform providing application security at the speed of DevOps.
As an Application Security Orchestration and Correlation (ASOC) tool, Maverix integrates Application Security Testing (AST) tools across a Software Development Life Cycle (SDLC) and performs correlation analysis of security issues found by the AST tools.
To keep the DevSecOps process under control, Maverix performs an additional function to collect development and security data from all the software engineering and AST tools integrated to the DevSecOps system. This functionality helps implement DevSecOps data analytics and enables intelligence within it using AI.
So, the main Maverix product features are:
- Orchestration
- Correlation
- Intelligence
Let’s briefly touch on these three key Maverix features.
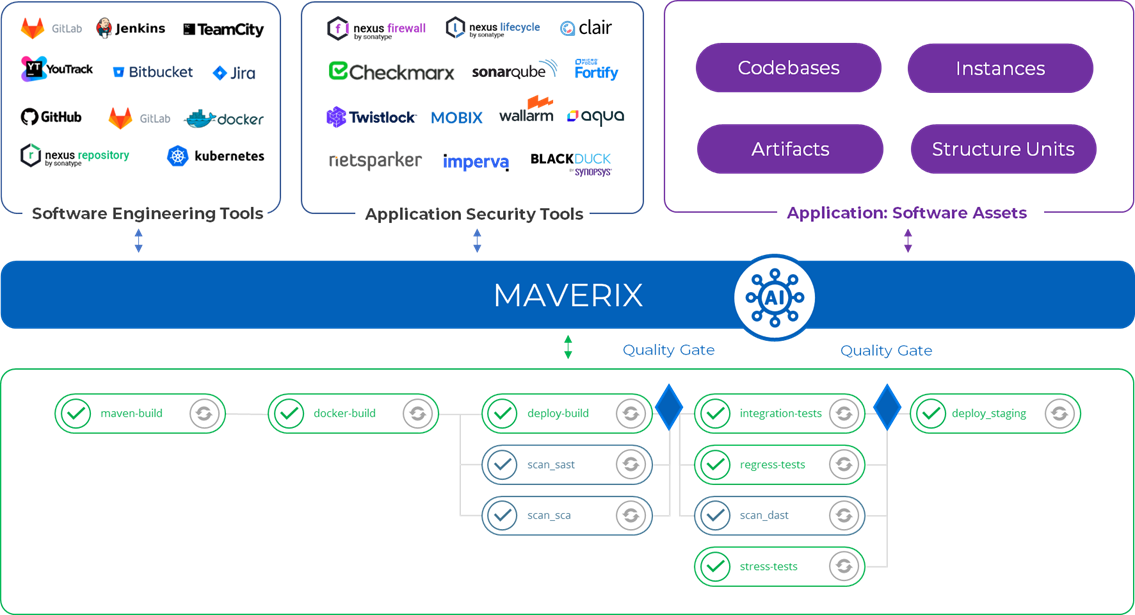
Orchestration
Maverix takes complete control of the application security testing process through integration with software development and AST tools. It is a "one-stop-shop" for integrating third-party tools into a united software development cycle as well as for configuring them.
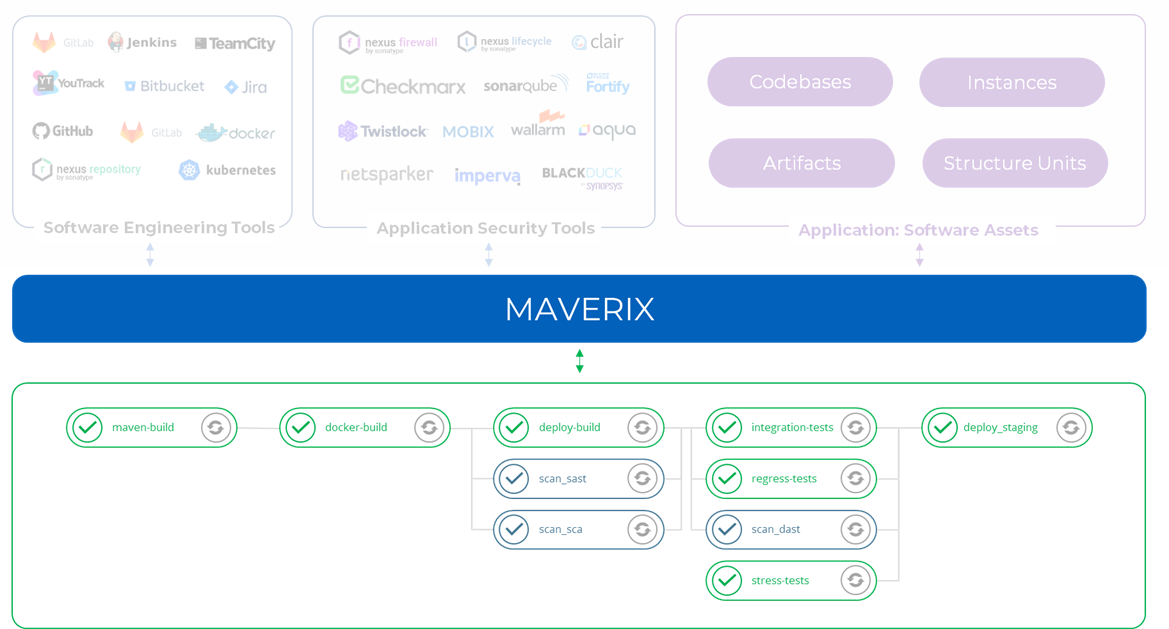
Integration with Software Engineering and AST tools
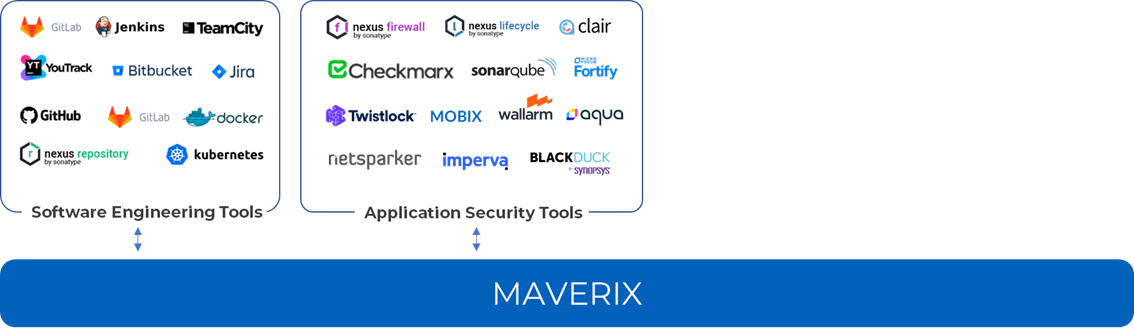
Maverix connects different entities into a seamless system. The first step is to connect two sets of tools to the platform – software engineering tools and AST tools. Maverix provides out-of-the-box integration with them:
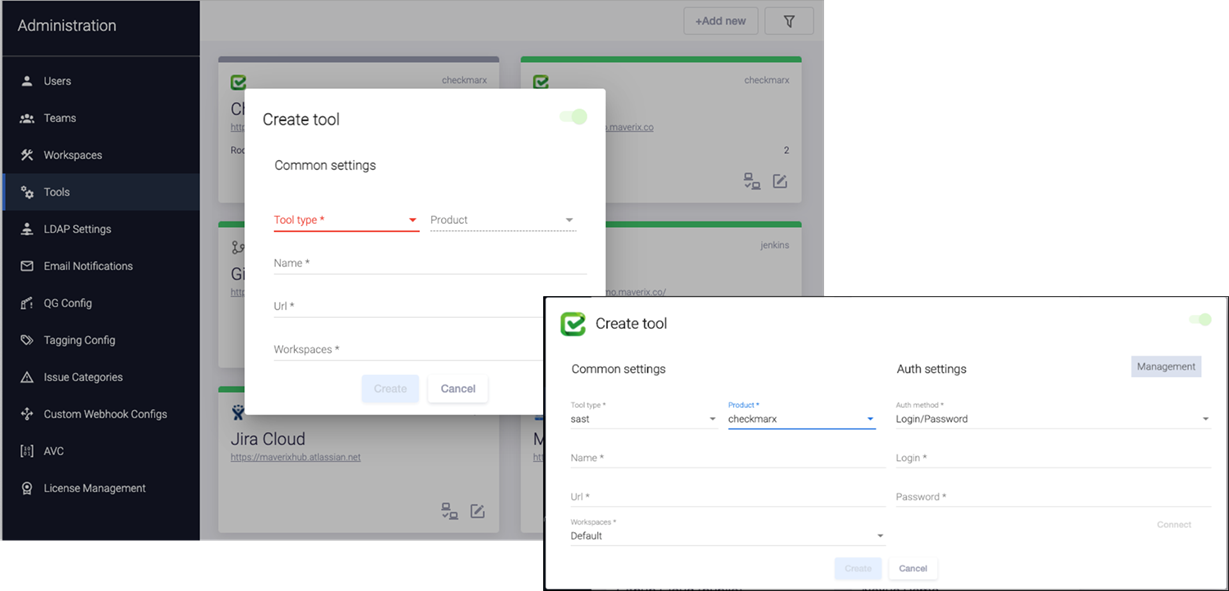
To connect a tool from the Maverix UI, you only need to make a few clicks and configure the tool settings. Just click the +Add new button to connect to a new tool, and enter URL to access the tool and your credentials:
The list of software engineering tools grouped by DevSecOps practices is as follows:
- Orchestration (CI) tools:
- JetBrains TeamCity.
- Jenkins.
- GitLab CI.
- Version Control Systems (VCS):
- Atlassian Bitbucket.
- GitLab.
- Any VCS with a git interface.
- Artifact Repository:
- Sonatype Nexus Repository Manager.
- GitLab Repository.
- File storages with HTTP/HTTPS access.
- Defect Tracking Systems (DTS):
- Atlassian Jira.
- JetBrains YouTrack.
- Workspaces:
- Atlassian Confluence.
The list of AST tools grouped by practices:
- Static Application Security Testing (SAST):
- Checkmarx.
- Micro Focus Fortify.
- SonarQube.
- DerScanner.
- Software Composition Analysis (SCA):
- Sonatype Nexus IQ.
- Container and Kubernetes Security (CKS):
- Clair.
- Aqua.
- Dynamic Application Security Testing (DAST):
- Netsparker.
- Wallarm FAST.
- Mobix (mDAST).
- Penetration Testing:
- Burp Suite.
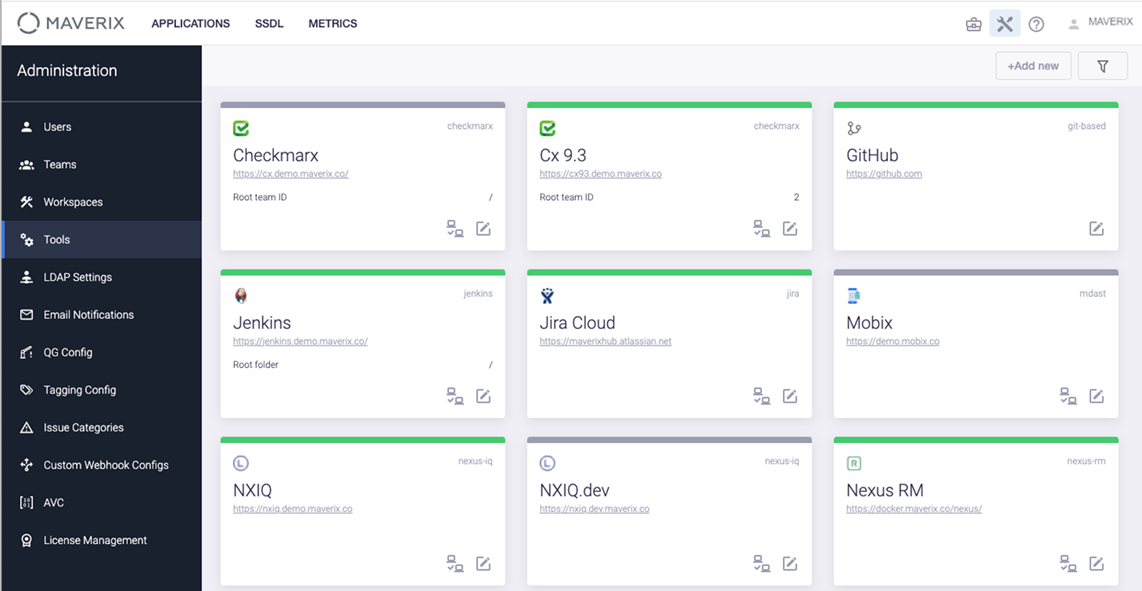
All connected tools are available in the Maverix UI under the Tools menu item. The parameters of each of them can be viewed and configured:
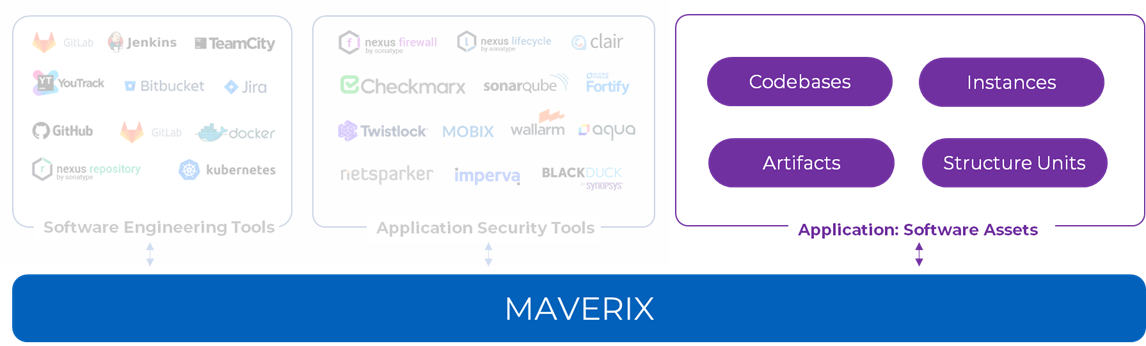
Software Assets Onboarding
Next, we need to connect the applications themselves and their assets, such as codebases, artifacts, application instances, and structure units. Maverix is exactly focused on ensuring the security of the developed applications. The security of these software assets is scanned by AST tools.
Onboarding of software assets can be performed either automatically using special Command Line Interface (CLI) scripts or manually. During automated onboarding, the scripts add information to Maverix about applications, their codebases, artifacts, and so on.
You can add and configure software assets manually using the Development menu item:
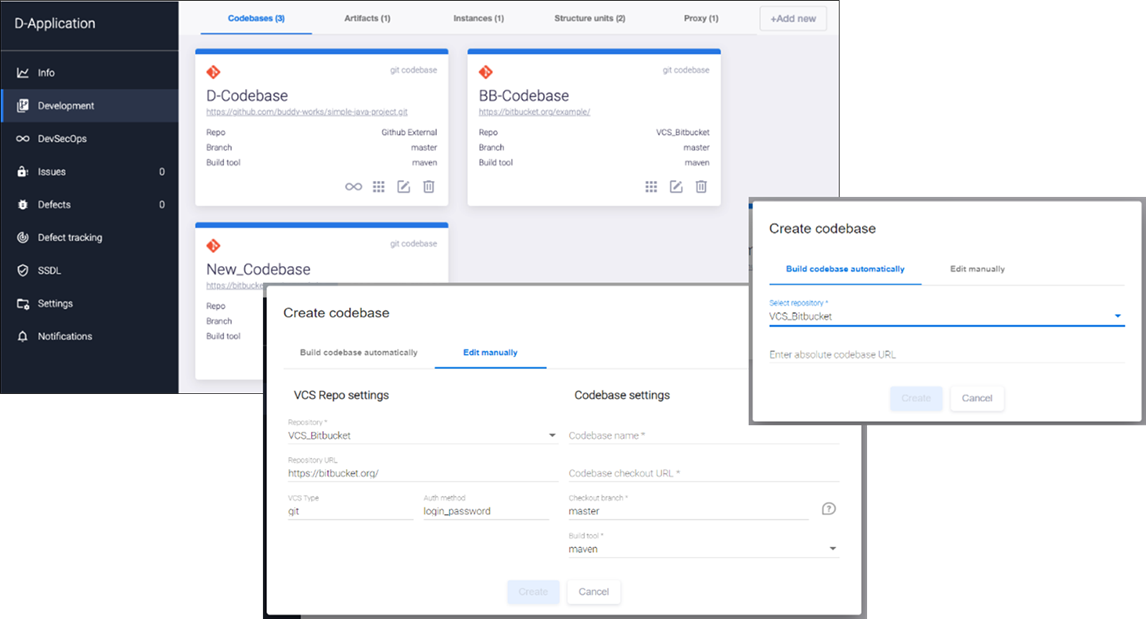
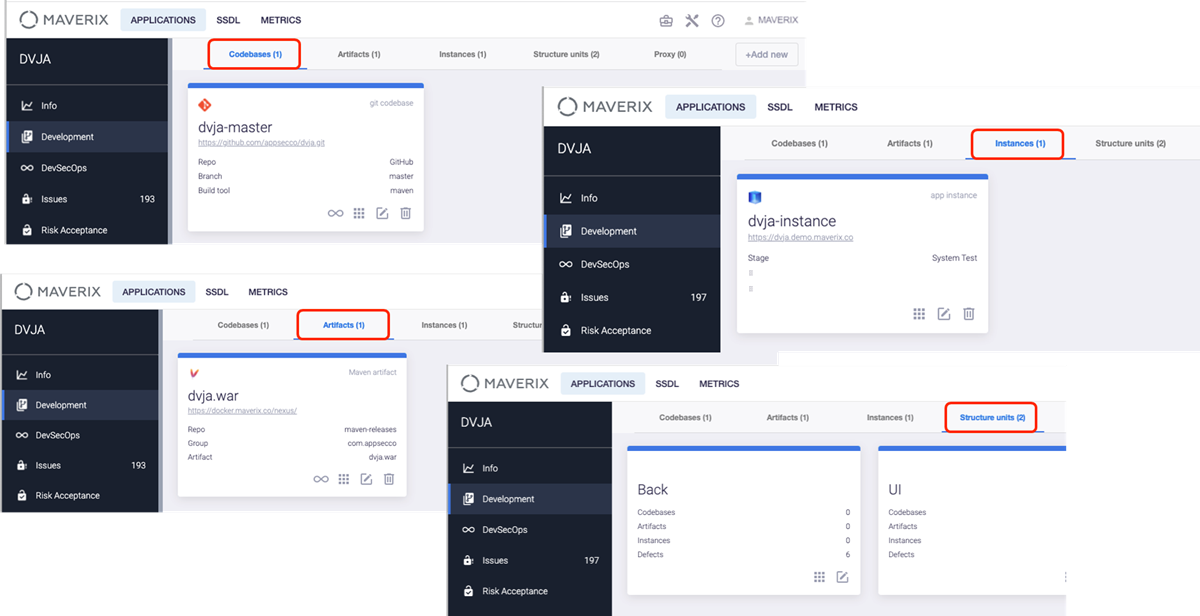
The Development page contains information about application codebases, artifacts, instances, and structure units. The "structure unit" type of assets helps align the work with the application architecture (modules, components, or microservices):
Security Pipelines Management
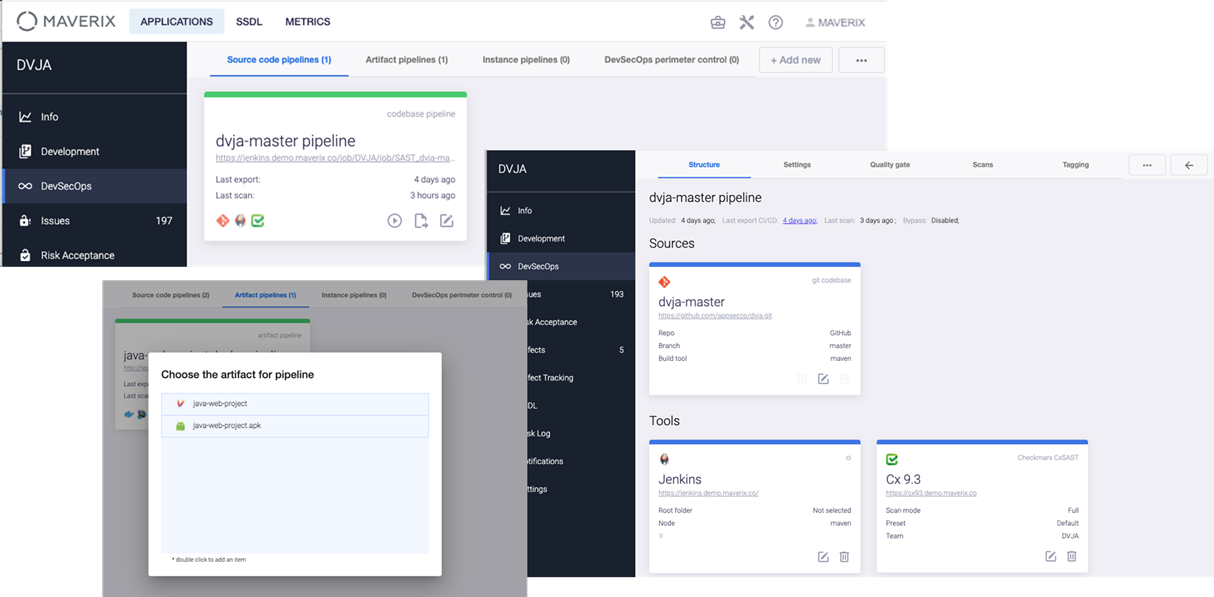
So, now we are all set to configure and run the CI/CD pipelines. In Maverix, we have not just CI/CD pipelines, but security pipelines with additional security checks.
The DevSecOps page is for working with the application security pipelines. Maverix makes it easy to create a security pipeline based on an existing CI/CD pipeline by adding one or more security checks. The security pipeline can be created automatically using an existing security pipeline template.
In Maverix, the security pipeline can be viewed as several cards. The Sources area shows the asset to be scanned, and the Tools area shows the security pipeline tool chain.
Security Quality Criteria Management
Maverix implements Quality Gates to control the results of security scans. First, it automatically checks the scan results and deploys the build only if the Quality Gate criteria are met.
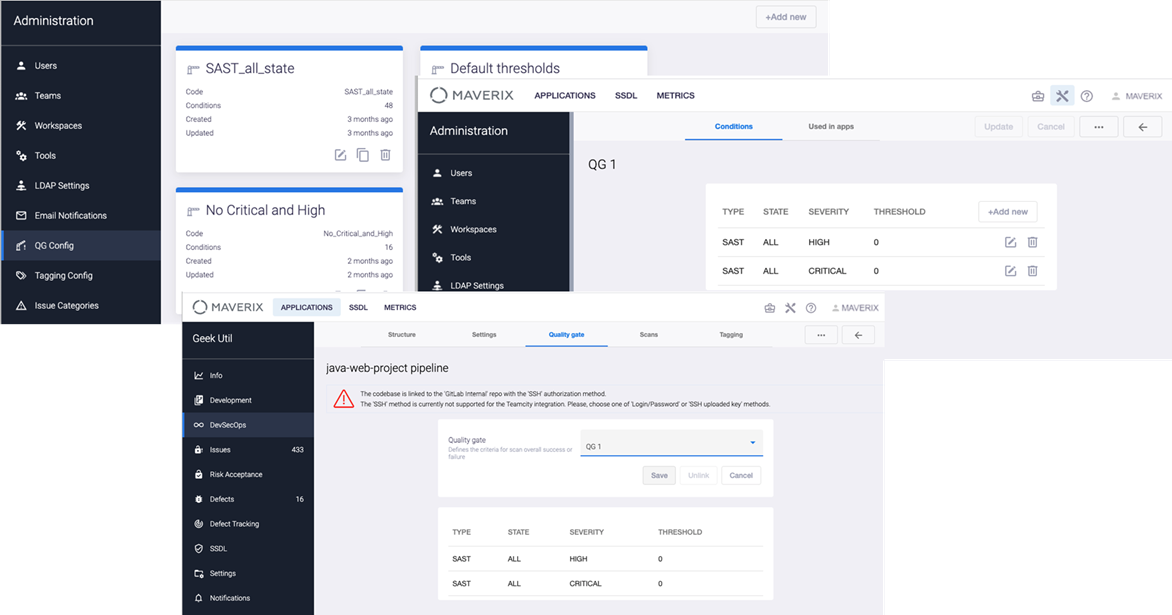
Suppose an application build should have no high and critical vulnerabilities. In this case, Quality Gate should be defined as follows: zero in the high severity and critical severity thresholds.
Select the QG Config menu item to configure Quality Gates. To add Quality Gate to the security pipeline, go to the configuration of that pipeline under the DevSecOps menu item, and select the existing Quality Gate profile.
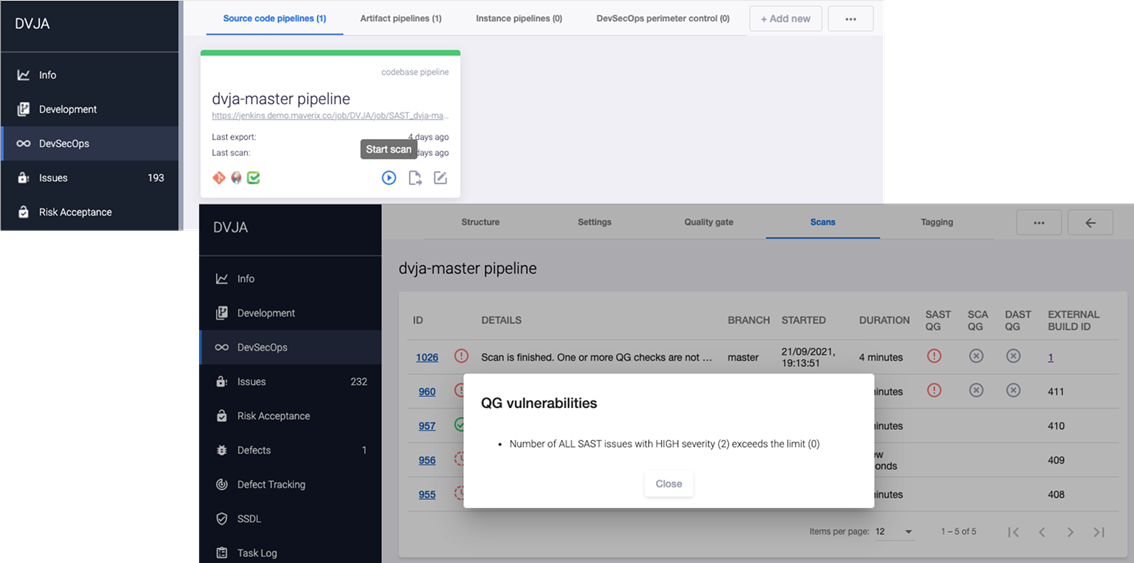
Security Pipeline Run
Click the Start scan icon at the bottom right of the security pipeline card to manually start security scan. Select the Scans tab to get details about the scan results. The scan status in relation to the QG is displayed in the SAST QG, SCA QG, and DAST QG fields. The detailed QG results are displayed is a special window.
Correlation
Gathering Security Issues from AST Tools
When a security scan is complete, the security issues are imported into Maverix from AST tools.
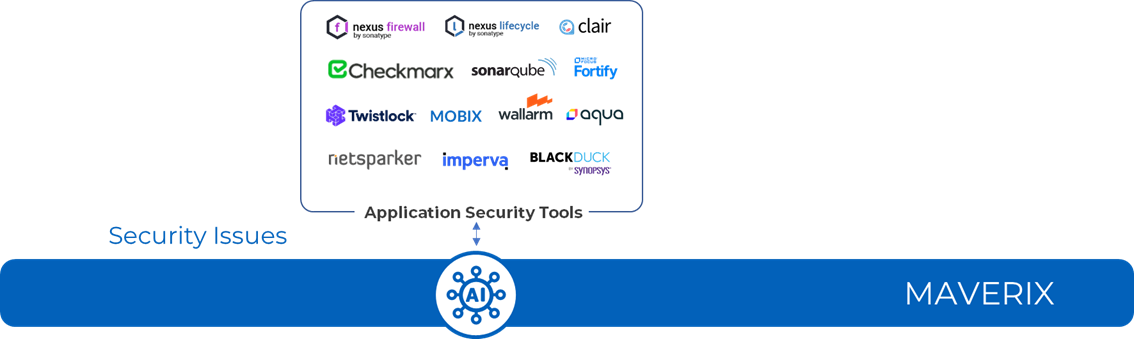
With Maverix UI, you can work with security issues from all AST tools. Maverix provides the standardization of security issue description, the grouping and consolidation of security issue data into a single workspace.
Select the Issues menu item. Each issue is presented as a separate line. Click the security issue ID to access detailed information about the issue, including recommendations on how to fix it.
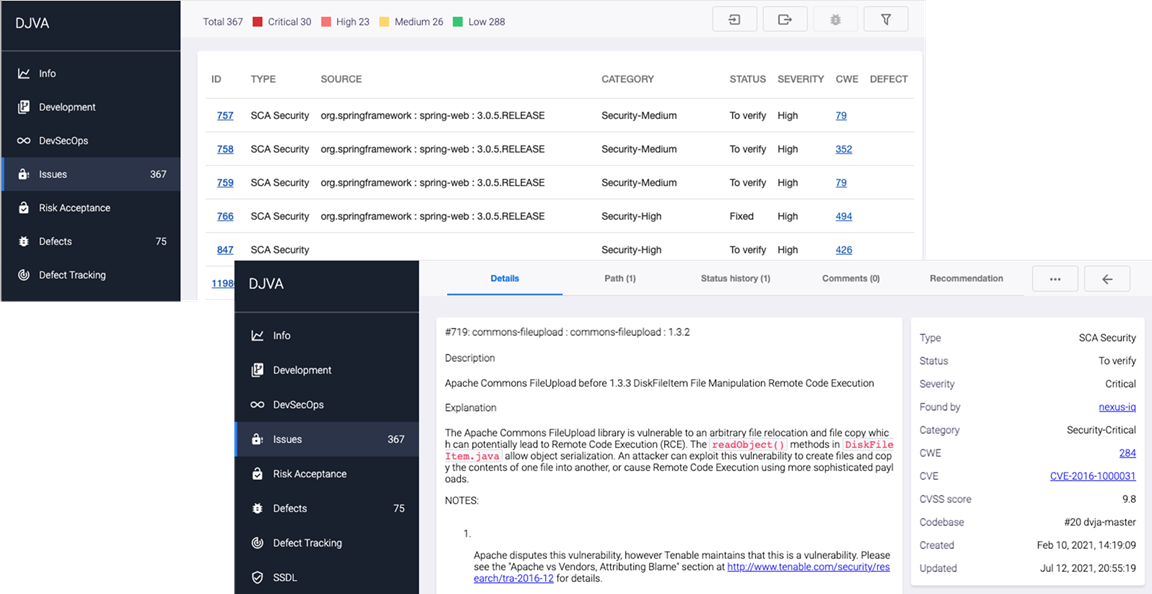
Handling Security Issues
All security issues detected during security scans are analyzed and triaged by Maverix.
First, Maverix analyzes security issues using the AI-based Application Vulnerabilities Correlation (AVC) model. AST tools usually generate dozens or hundreds of security issues. Not all these issues are unique and important. The AVC status indicates whether the issue is true positive or false positive by the Maverix assessment and provides the quantitative assessment.
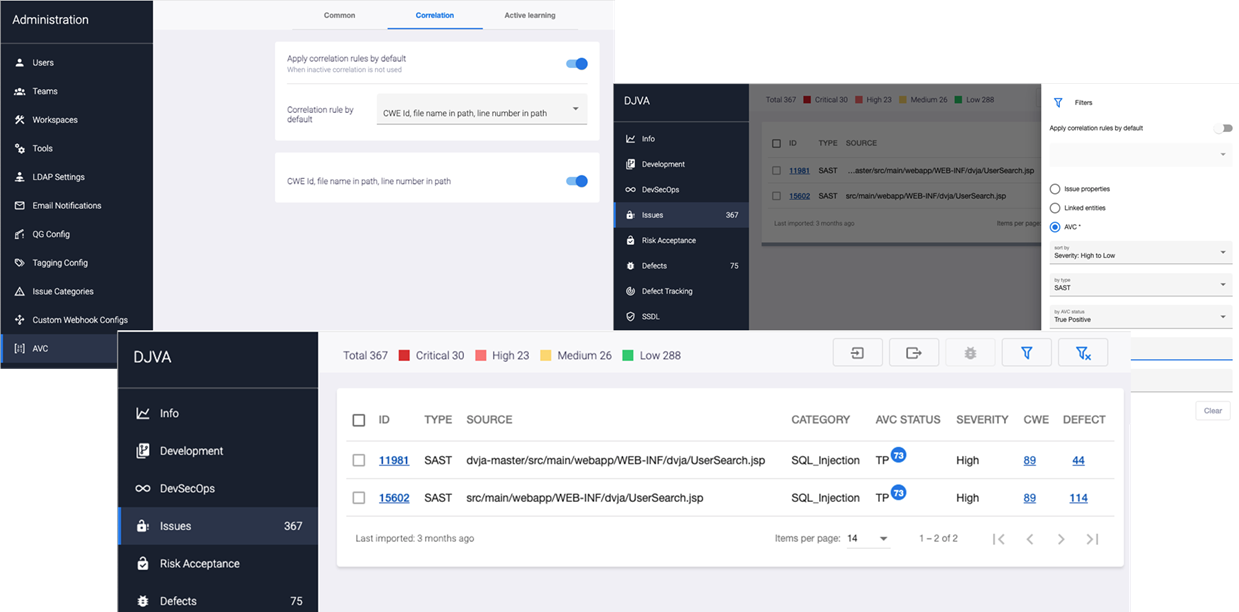
Second, Maverix triages the identified security issues based on the correlation model implemented in the system. It groups similar issues that can be resolved simultaneously to treat them as a single issue.
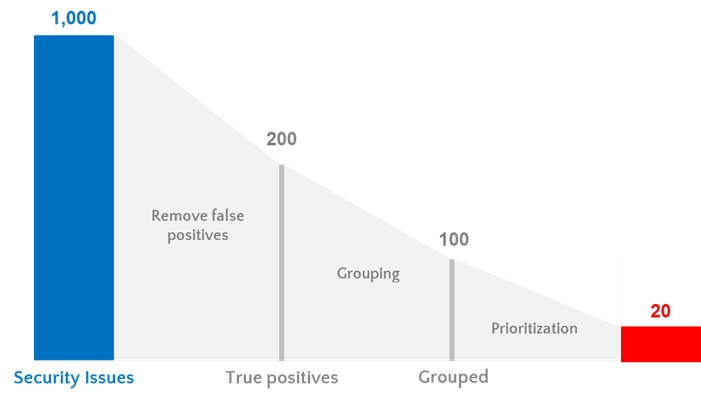
After completing the first two steps, you should prioritize security issues. Maverix allows you to prioritize all issues according to their severity, from high to low.
Together, these three steps make it much easier to work with the security issues found:
Handling Security Defects
With Maverix, security issues can be quickly triaged, grouped, and submitted as defects in DTS.
Maverix provides bidirectional synchronization of the status of security defects with DTS. You can configure the synchronization settings on the Defects Tracking page.
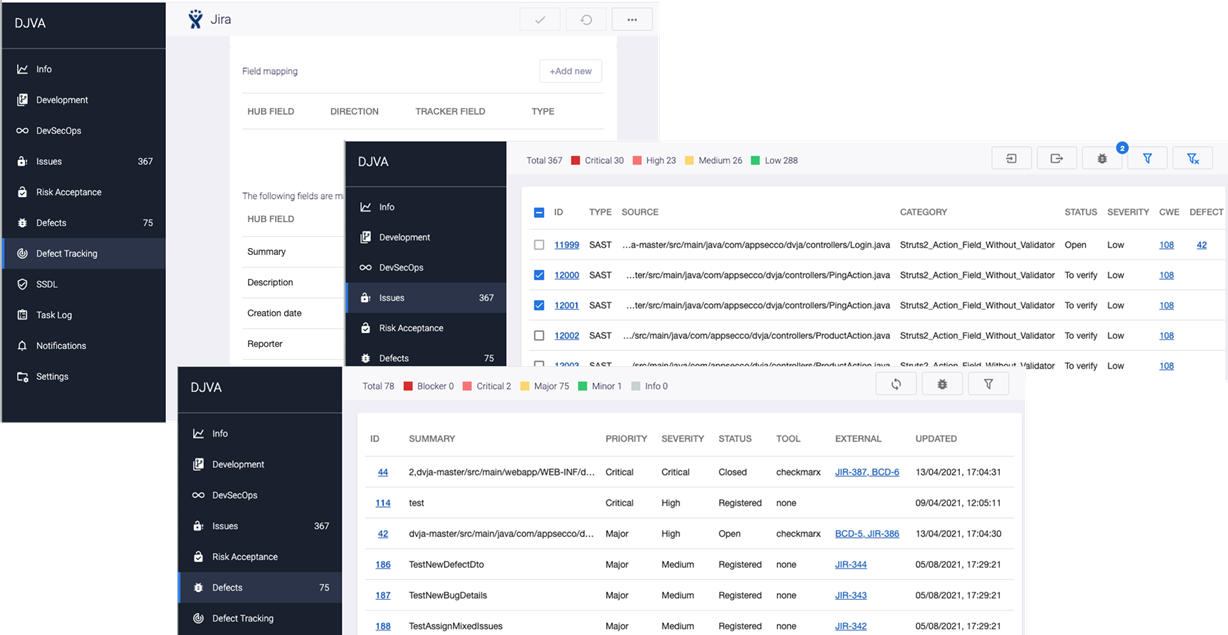
Each security defect is created based on one or several grouped similar security issues for further processing by the development team.
Intelligence
DevSecOps data analytics allows you to analyze the security status of applications across all teams and applications in the organization. Maverix aggregates engineering and security data in a data warehouse (DWH) and offers a set of metrics and dashboards to work with that data.
Select the Metrics menu item at the top left of the Maverix UI. Choose a required metric and configure the filters.
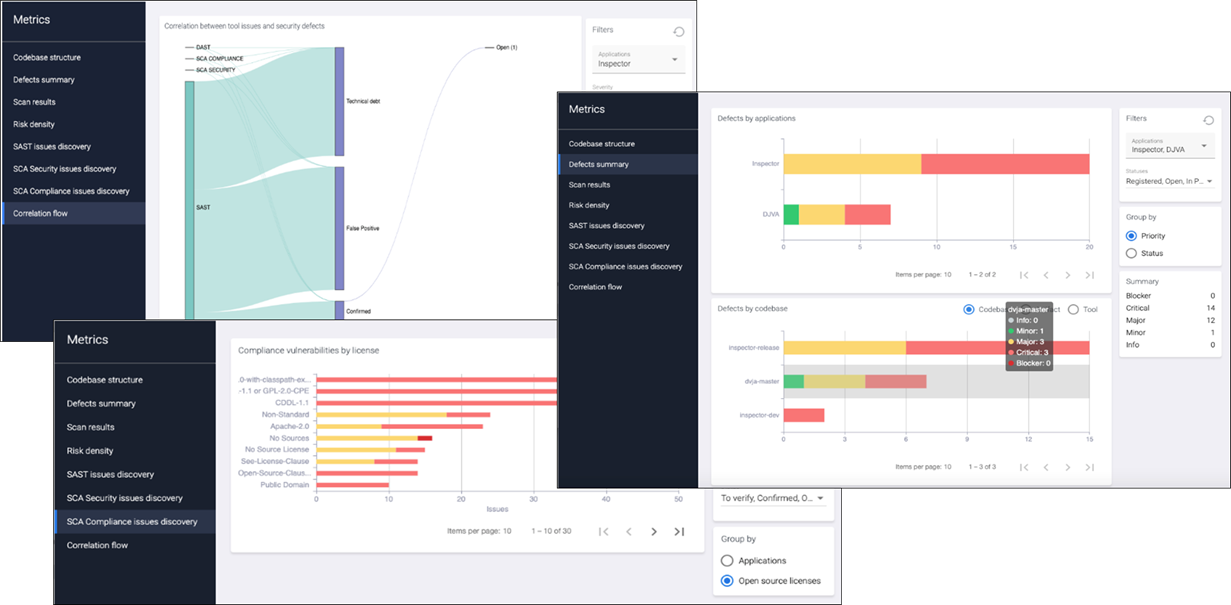
Data collection, aggregation, and analysis help implement data-driven secure application development. This gives management, development, operations and security teams complete visibility into security and software engineering.