Security pipeline settings
Select the Settings tab to change the security pipeline settings.
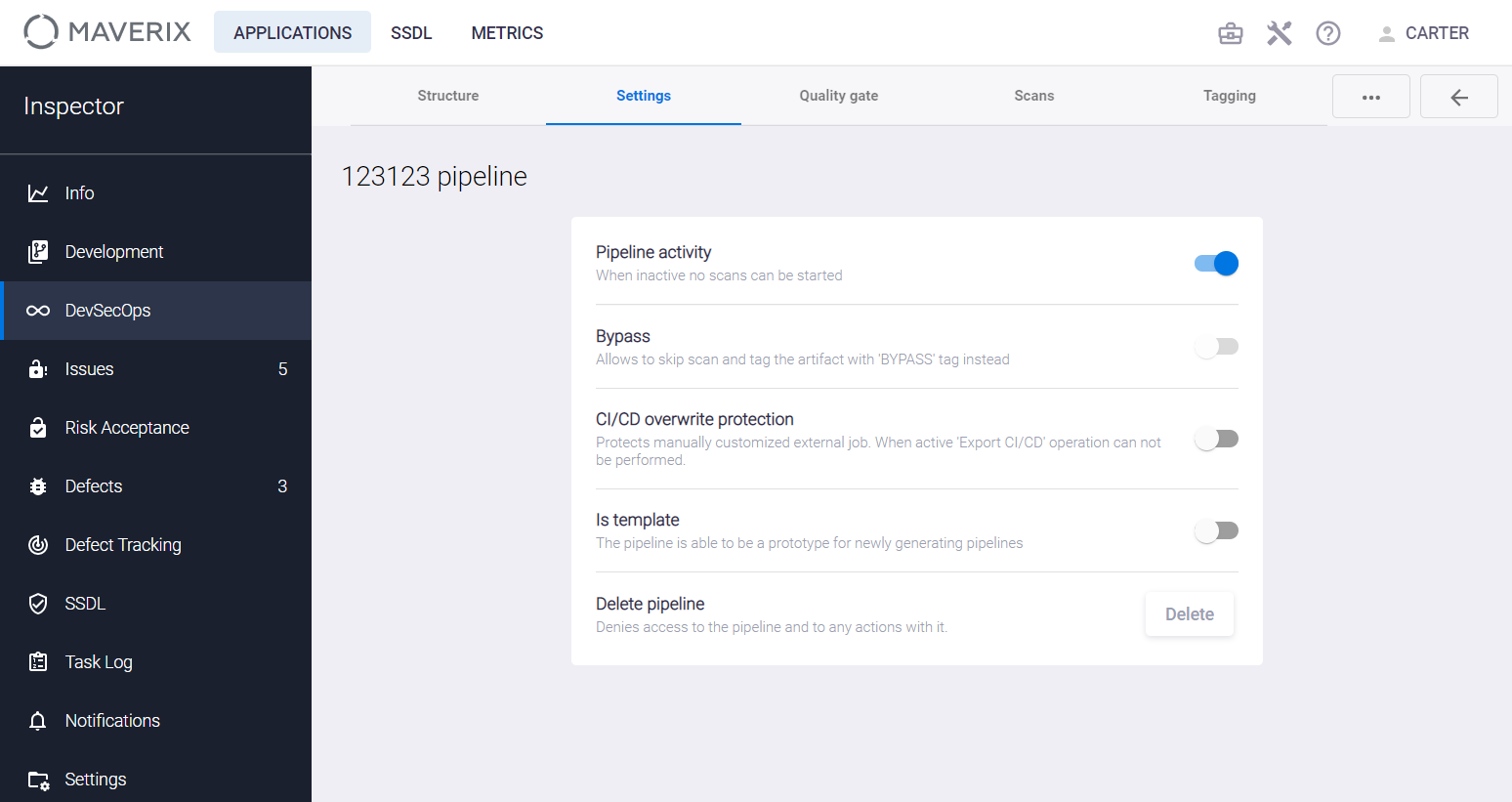
On this tab, you can use the selectors to change the following settings:
- Pipeline activity. If the selector is off, the scan can’t be performed in this security pipeline. The security pipeline status is indicated with a colored line at the top of the security pipeline card. If the line is green (the selector is on), the scan can be performed in the security pipeline.
If the line is gray (the selector is off), the scan can’t be performed in the security pipeline.
- Bypass If this selector is on, no scanning is performed when starting the security pipeline. The artifact will be marked with the BYPASS tag, and the Bypass is enabled
 icon will appear in the security pipeline card
icon will appear in the security pipeline card
 |
This functionality is available only after adding a tagged artifact to the security pipeline, see the "Artifact Security Pipeline" section. |
When you start such a security pipeline, a confirmation notification appears in the lower right corner of the user interface, but no actual scan is performed. A corresponding warning is displayed in the scan history (the Scans tab).
For example, you can use this functionality during on-boarding processes using Meta-runner, if you only want to scan the artifact, but not the code base. In this case, the Bypass option is activated for the code base security pipeline.
- CI/CD overwrite protection. This selector blocks the export of the security pipeline to the CI/CD tool using the Export CI/CD menu item. This option protects the security pipeline settings from unwanted overwriting. The Overwrite protection is enabled
 icon appears in the security pipeline card.
icon appears in the security pipeline card.
- Is template. This option allows you to use this security pipeline as a template for creating new ones. The template pipeline
 icon appears in the security pipeline box. It's important to note that a predefined security pipeline template should be defined in Maverix to complete the on-boarding processes correctly (see the "On-boarding - automating Maverix integration into the development cycle " section). Any previously created for this application Security Pipeline of an appropriate type (for code bases, artifacts, etc.) can be used as such template. If several Security Pipelines of the same type are defined for an application, it is necessary to activate the "Is template" option for the selected security pipeline to complete the on-boarding in a predictable manner. That way, the newly created security pipelines for this application will automatically use the selected template.
icon appears in the security pipeline box. It's important to note that a predefined security pipeline template should be defined in Maverix to complete the on-boarding processes correctly (see the "On-boarding - automating Maverix integration into the development cycle " section). Any previously created for this application Security Pipeline of an appropriate type (for code bases, artifacts, etc.) can be used as such template. If several Security Pipelines of the same type are defined for an application, it is necessary to activate the "Is template" option for the selected security pipeline to complete the on-boarding in a predictable manner. That way, the newly created security pipelines for this application will automatically use the selected template.
- Delete pipeline. Click the Delete button to deny access to the security pipeline and any actions with it.