Security pipeline structure
In Maverix, each security pipeline is mapped to an application. The security pipeline performs security scans. Security pipelines provide automated application security testing for development, test, or production environments. Security pipelines run security checks during each engineering cycle.
Security pipelines are targeted to analyze three types of objects. Thus, there are three types of security pipelines:
- Source Code Security Pipeline.
- Artifact Security Pipeline.
- Application Instance Security Pipeline.
Security pipelines are generated in the orchestration tool (e.g., TeamCity) for a particular codebase/artifact/instance of application based on the configuration of software engineering and AST tools used.
It’s possible to start a security scan by clicking the Start scan ![]() button in the security pipeline card.
button in the security pipeline card.
Select the Applications menu item at the top left of the Maverix user interface to start work with applications and their security pipelines. Application cards appear on the screen.
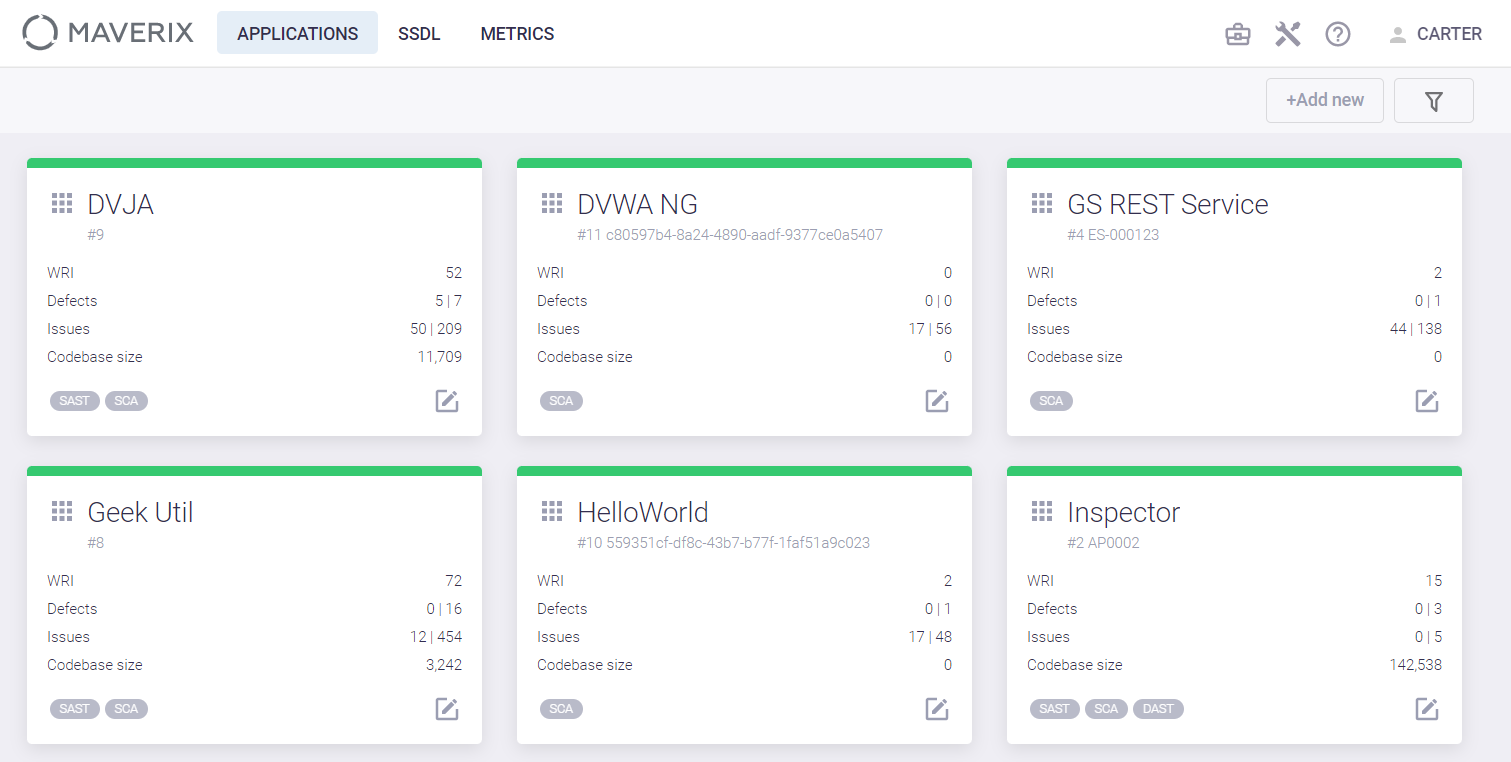
Click the edit icon  at the bottom right of the application card on the Applications page. The page with detailed information about this application appears. The application name can be seen in the top left corner of the page that appears. Click the DevSecOps menu item on the left. Three tabs with three types of application security pipelines appear.
at the bottom right of the application card on the Applications page. The page with detailed information about this application appears. The application name can be seen in the top left corner of the page that appears. Click the DevSecOps menu item on the left. Three tabs with three types of application security pipelines appear.
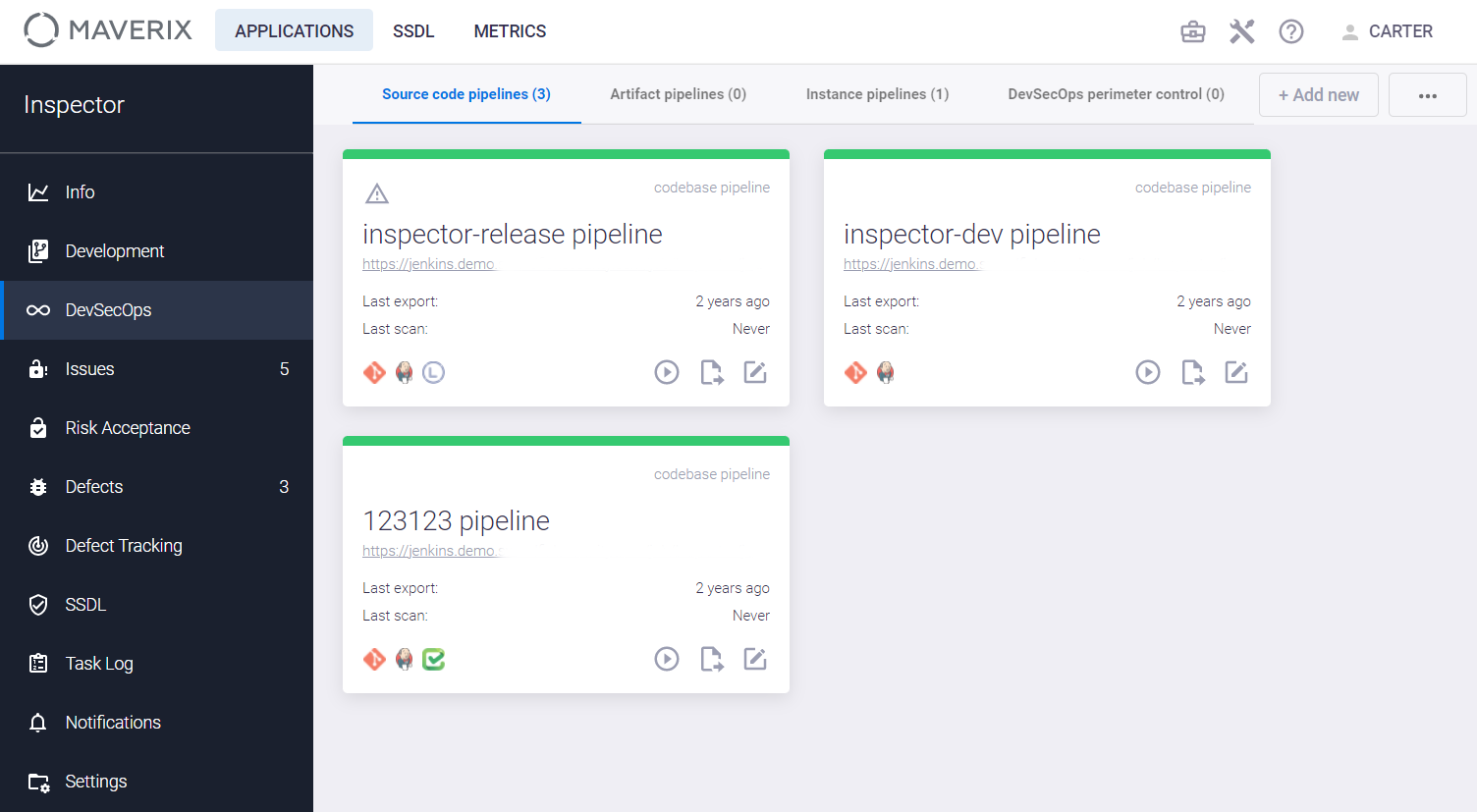
In addition to three tabs with the three types of security pipelines, there’s the DevSecOps perimeter control tab for working with proxy repositories. For more information, see the "Proxy repositories" section.
Click the edit  icon in the lower right corner of the security pipeline card to view or update information on that pipeline. For example, if you click the edit
icon in the lower right corner of the security pipeline card to view or update information on that pipeline. For example, if you click the edit  icon in a card on a source code security pipeline, you can get the following information about the pipeline on the Structure tab:
icon in a card on a source code security pipeline, you can get the following information about the pipeline on the Structure tab:
- VCS tool, codebase URL, branch type, build tool.
- Orchestration (CI/CD) tool and its URL.
- Security scan tool (e.g., Checkmarx) and a scan mode used (e.g., incremental).
- General information: the last update date, the last export to CI/CD, the last scan date, status of the security issue auto-import.
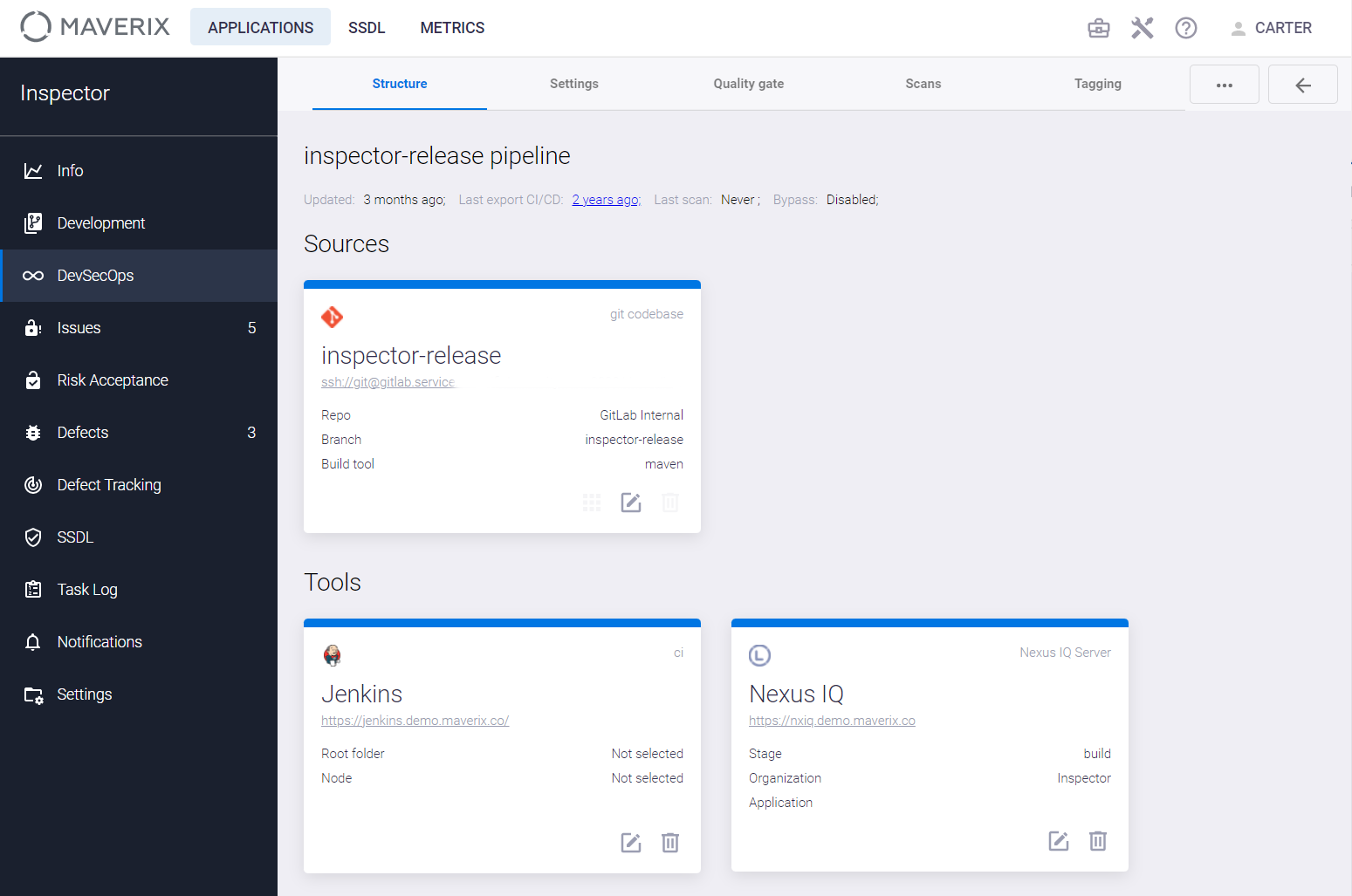
The security pipeline of source code contains several cards—one for each tool in the pipeline. For example, the security pipeline shown above contains three parts, represented as three cards:
- Code bases (source code).
- Orchestration (CI/CD) tools.
- AST tool (Checkmarx).
The configuration process of the security pipeline includes the following steps:
- Selection of software engineering and AST tools.
- Configuration of each selected tool.
- Definition of quality criteria and creation of Quality Gates (for more information, see the "Adding Quality Gate to Security Pipelines" section of this document and the "Quality Gates" section of Application Administrator Guide).
A set of software engineering and AST tools used depends on the available licenses. Each tool's configuration is defined in Maverix. As an example, consider the Checkmarx tool configuration. Click the Edit tool  icon at the bottom right of the Checkmarx card. The Update SAST scan config window appears.
icon at the bottom right of the Checkmarx card. The Update SAST scan config window appears.
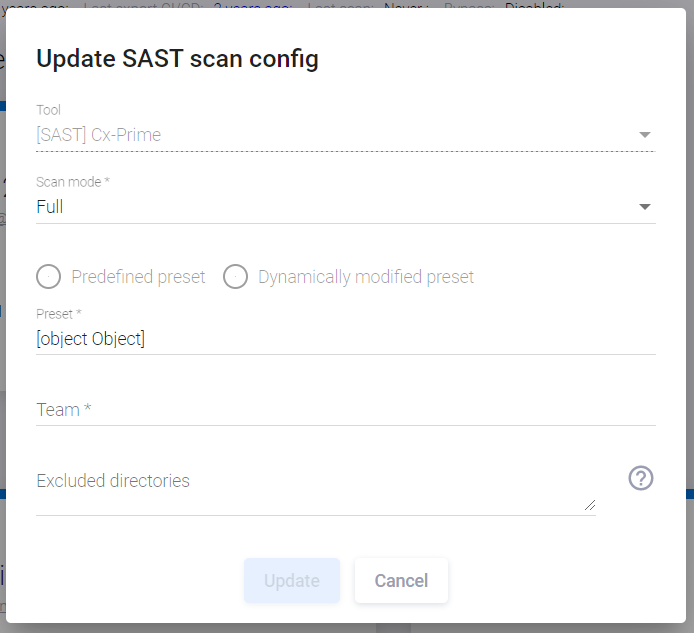
Define the Checkmarx configuration in this window:
- Scan mode. Select the Full or Incremental option from the drop-down menu.
- Select Predefined preset/Dynamically modified preset to use for the scan. For more information on Dynamically modified presets for Checkmarx, see the "Source Code Security Pipeline" section.
- Preset. Select the rules defined in the Checkmarx tool (Checkmarx Default, Checkmarx Express, All, High and Medium, etc.). This field is active when Predefined preset is selected.
- The Root team is defined in the Checkmarx settings.
- Select a structural unit from the Team drop-down menu.
- Excluded directories Directories specified here will not be scanned during a security scan.
Click the Update button to save the Checkmarx tool configuration. The Checkmarx card displays the new settings after configuration.
Note that Maverix automatically updates the settings in the Checkmarx tool itself. No additional user action is required.
A Maverix user with Manager permissions can perform the following actions on a security pipeline by clicking the Actions ![]() button in the right upper corner and selecting one of these actions from the drop-down menu:
button in the right upper corner and selecting one of these actions from the drop-down menu:
- Export a security pipeline to the CI/CD tool.
- Start scan (run a security pipeline).
- Add a new element (tool) to the security pipeline.